In today’s world, security has become a paramount concern for organizations across various industries. Whether it’s an office building, a manufacturing facility, or a research institution, ensuring the safety of employees, visitors, and assets is crucial. One effective measure in validating the identity of individuals entering a facility is using a government ID. This blog explores the significance of government ID in facility access, the risks impostors pose, and how implementing this is valid.

The Risks of Impostors and the Need for Valid Identification

Security breaches and unauthorized access to facilities have raised concerns about the effectiveness of traditional visitor sign-in processes. Unauthorized individuals, intentionally or unintentionally, can gain entry by providing false information or assuming someone else’s identity. This compromises the facility’s security and poses potential threats to personnel and sensitive information.
To combat these risks, government ID is a reliable means of verifying an individual’s identity. Government-issued identification documents, such as driver’s licenses or passports, carry higher trust and authentication. These IDs contain embedded security features, making them difficult to replicate or forge. By scanning and validating government IDs, organizations can ensure that only authorized individuals can access their premises.
Real-World Examples of Security Compromises
Numerous incidents in the past have highlighted the vulnerabilities organizations face when they fail to implement robust identification procedures. In 2014, an imposter disguised as a delivery person accessed a high-security government facility in the United States. The imposter, lacking valid identification, bypassed security measures and entered the building, putting sensitive information at risk.
Similarly 2019, a significant financial institution fell victim to an impostor who gained unauthorized access to restricted areas within their headquarters. The individual presented a fake visitor badge and pretended to be a contractor. The absence of government ID verification enabled this breach and highlighted the need for more vital identification protocols.
Statistics and Studies Reinforcing the Importance of Government ID

Research and studies further emphasize the necessity of government ID in ensuring facility security. According to a survey conducted by the Ponemon Institute, 62% of respondents reported that they had experienced unauthorized entry into their facilities within the past year. Among those incidents, many involved impostors using false identities or exploiting lax identification processes.
Furthermore, a study published in the Journal of Applied Psychology revealed that organizations that implemented robust ID verification systems experienced a significant reduction in security breaches. This demonstrates the effectiveness of using government ID to validate the identities of individuals entering a facility and deter potential impostors.
Enhancing Security and Efficiency with Government ID
Implementing a system that scans and validates government IDs offers several benefits beyond heightened security. It streamlines the visitor management process, reduces human error, and enhances operational efficiency.
By automating the identification process, organizations reduce their reliance on manual data entry, minimizing the chances of errors or discrepancies in visitor information. Additionally, integrating government ID scanning with visitor management systems enables real-time cross-referencing against watchlists or employee databases, providing an added layer of security against potential threats.
Using government ID in facility access also aligns with best practices in other security-sensitive environments, such as airports. Airports worldwide have implemented stringent ID verification protocols to ensure the safety of passengers and staff. By drawing upon these successful practices and adapting them to facility access control, organizations can adopt proven strategies and leverage technological advancements to mitigate security risks effectively.
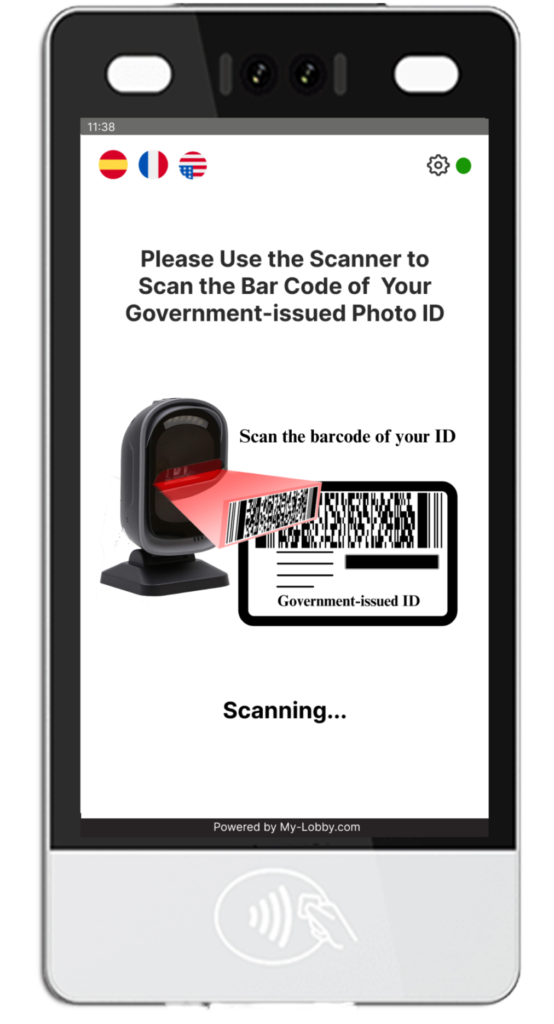
Economic Viability and Labour Market Considerations
In the past, the cost of implementing advanced ID verification technology was a deterrent for many organizations. However, with the advancements in artificial intelligence (AI) technology and the decreasing costs associated with its implementation, the barrier to entry has significantly diminished. AI-powered scanning systems can accurately verify government IDs in real time, making it an affordable and efficient solution for businesses of all sizes.
Moreover, the rising labor costs and the scarcity of qualified security personnel pose challenges for organizations in maintaining a robust security program. By automating the identification process, organizations can reduce their reliance on dedicated security staff for manual ID verification, enabling them to allocate resources more strategically and address other critical organizational needs.
Conclusion
Its clear to see the importance of validating individuals’ identities when entering a facility cannot be overstated. Government ID serves as a trusted and reliable means of verification, mitigating the risks associated with impostors and unauthorized access. By implementing ID scanning systems, organizations enhance their security programs, reduce the likelihood of security breaches, and protect personnel, assets, and sensitive information.
In addition to increasing security, using government ID in facility access brings about operational efficiencies by streamlining visitor management processes and reducing human error. With the availability of cost-effective AI technologies, organizations can now implement robust ID verification systems that were previously out of reach.
As organizations adapt to the evolving security landscape, integrating government ID scanning into facility access control becomes critical to ensure a safe and secure environment. By embracing this technology, organizations can protect their interests, maintain compliance with regulations, and establish a strong foundation for comprehensive security practices.
